Which of the following words best describes the pardoners treatment of the host. The mode of transmission can include direct contact droplets a vector such as a mosquito a vehicle such as food or the airborne route.

Uk Health Security Agency On Twitter Thread The Chain Of Infection Describes The Process That Allows An Infectious Agent To Move From Host To Host If All The Links In The
Former black hat C.
. Which of the following describes mode of transmission. Wireless and wired networks are both susceptible to rfi. Group of answer choices The method by which a pathogen is transmitted A description of the susceptible host A process for killing pathogens The way a pathogen is treated once it enters the body 1.
A Unauthorized individuals can deny service to a computing system by overwhelming the system with login attempts. And are a portal of exit. Which of the following best describes the order of occurrence of the infection cycle.
For each of the following risk factors and health outcomes identify whether they are necessary causes sufficient causes or component causes. The internal client and the external server. The and the are the best type of susceptible host.
A penicilloyl polylysine skin test yields positive results. The external server and the proxy server. The internal client and the proxy server.
A 13-year-old male with cystic fibrosis develops repeated episodes of pneumonia resulting in multiple hospitalizations. Susceptible hosts differ from the general population because they are far more likely to. The agent Dracunculus medinensis develops in the intermediate host fresh water copepod.
The susceptible host has multiple portals of entry such as the mouth or a syringe. Question 117 of 176. Which of the following best illustrates the type of hypersensitivity reaction.
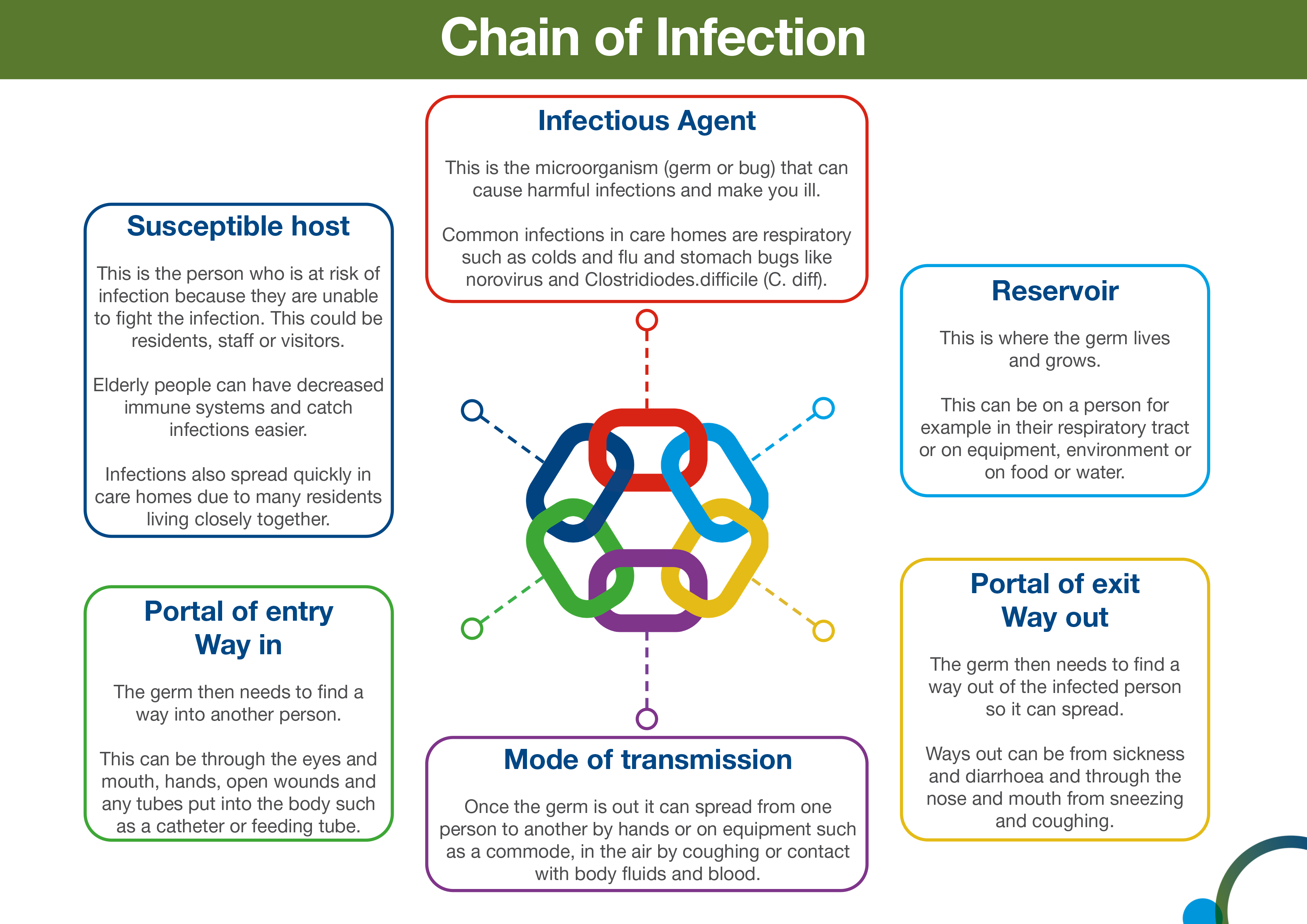
Direct contact between infectious host and susceptible host or indirect transmission which involves an intermediate carrier like an environmental surface or piece of medical equipment. Previous antibiotic treatment resulted in severe rash fever and systemic anaphylaxis almost immediately. SUSCEPTIBLE PERSON HOST A susceptible or non-immune person is one who has little resistance against a particular organism and who if exposed to this organism is likely to contract disease.
Select one of the following. Malicious hacker Answer 1. Immunity is the type of immunity gained through vaccination.
Which of the following best explains how devices and information can be susceptible to unauthorized access if weak passwords are used. A Toxoplasmosis B Staphylococcus Aureus C Hepatitis 8 D Creutzfeldt Jakob diseas e or Mad Cow s Disease. Source mode of transmission susceptible host John Snow Robert Koch Kenneth Rothman For each of the following identify the appropriate letter from the time line in Figure 127 representing the natural history of disease.
Which of the following sets of words best completes the following sentence. A white-hat hacker is a good guy who uses his skills for defensive purposes. In this model the disease results from the interaction.
Describe its causation in terms of agent host and environment. Typhus Lyme disease and Rocky Mountain spotted fever are from the family. An example of a prion would be.
в Unauthorized individuals can exploit vulnerabilities in compression algorithms to determine a. The triad consists of an external agent a susceptible host and an environment that brings the host and agent together. Read the Anthrax Fact Sheet on the following 2 pages then answer the questions below.
The external server and the firewall. By contrast an immune person is one who has a high degree of resistance to the organism and who when exposed does not develop the disease. PORTAL OF ENTRY The opening where an infectious disease enters the hosts body such as mucus membranes open.
Which of the following statements best describes a white-hat hacker. CompTIA Security Exam 2021. Which of the following best describes the order of occurrence of the infection cycle.
MA 10110 Final Study Guide 1. Among the simplest of these is the epidemiologic triad or triangle the traditional model for infectious disease. A susceptible host is a member of a species population who is at risk of becoming infected with a certain disease due to a variety of reasons.
Which of the following best describes a bastion host. The user in unable to authenticate because they are outside of the organizations mobile geofencing configuration. Former grey hat D.
A number of models of disease causation have been proposed. A an animal or insect that may infect a person B both A and C C an elderly or young person who is vulnerable to infection D a virus. The laptop is still configured to connect to an international mobile network operator.
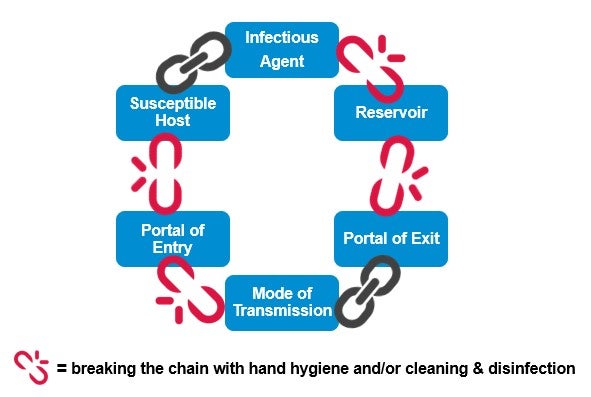
Once a circuit level gateway verifies the users logon it creates a virtual circuit between. 1 Susceptible host 2 Portal of exit 3 Infectious agent 4 Reservoir host 5 Means of transmission 6 Portal at entry a 123456 b 234561 c 342561 d 432651. Which areas of the world are most susceptible to desertification.
A security audit performed on the internal network. Are caused by a scraping away of the skins surface and are susceptible to infection.

Covid 19 The Chain Of Infection Transition From Hospital To Home Cloroxpro

0 Comments